 Check Point Endpoint Security
Check Point Endpoint Security
A guide to uninstall Check Point Endpoint Security from your PC
Check Point Endpoint Security is a Windows application. Read more about how to uninstall it from your computer. The Windows version was developed by Check Point Software Technologies Ltd.. More information on Check Point Software Technologies Ltd. can be found here. Please follow http://www.checkpoint.com if you want to read more on Check Point Endpoint Security on Check Point Software Technologies Ltd.'s web page. Check Point Endpoint Security is typically installed in the C:\Program Files (x86)\CheckPoint\Endpoint Security Agent folder, however this location may vary a lot depending on the user's option when installing the application. MsiExec.exe /X{D84FA1D7-7063-4021-B1E3-3C002F53F516} is the full command line if you want to remove Check Point Endpoint Security. The program's main executable file is named CheckConnectivity.exe and occupies 1.64 MB (1720080 bytes).Check Point Endpoint Security contains of the executables below. They take 22.68 MB (23779904 bytes) on disk.
- CheckConnectivity.exe (1.64 MB)
- cpda.exe (6.81 MB)
- cppsm_tool.exe (231.44 KB)
- CPRegSvr.exe (90.24 KB)
- cptray_mini.exe (719.94 KB)
- cpvinfo.exe (71.74 KB)
- epwirfix.exe (50.81 KB)
- IDAFServerHostService.exe (790.44 KB)
- PushOperationsRepairHelper.exe (623.44 KB)
- cpinfo.exe (544.44 KB)
- cpinfoUI.exe (223.94 KB)
- cpinfo_uploader.exe (6.27 MB)
- EPHealthMonitor.exe (954.69 KB)
- tracelog.exe (85.94 KB)
- tracelog.exe (93.44 KB)
- nginx.exe (3.59 MB)
The current page applies to Check Point Endpoint Security version 87.62.2002 only. Click on the links below for other Check Point Endpoint Security versions:
- 81.00.7062
- 86.80.0109
- 8.4.196
- 8.6.533
- 8.2.965
- 80.94.6538
- 80.72.0078
- 84.71.8708
- 80.70.0209
- 8.4.152
- 80.65.2516
- 8.2.897
- 84.30.6638
- 8.8.388
- 8.4.620
- 8.7.036
- 80.70.0363
- 80.72.0054
- 85.00.0017
- 84.00.5003
- 8.2.954
- 86.40.0169
- 84.70.8619
- 80.84.6075
- 8.4.213
- 86.30.0187
- 87.00.0022
- 80.95.6601
- 86.40.0242
- 80.94.6519
- 80.87.9201
- 87.31.1015
- 80.70.0247
- 85.20.1115
- 82.40.1102
- 80.83.5080
- 88.10.0220
- 86.01.1005
- 87.31.1016
- 86.25.5060
- 86.00.0007
- 80.85.7064
- 8.4.467
- 8.2.833
- 83.15.3054
- 82.30.0530
- 80.87.9250
- 87.30.0232
- 8.7.025
- 8.3.755
- 80.87.9084
- 86.51.1013
- 88.00.0188
- 8.2.898
- 8.8.255
- 84.60.8134
- 8.2.923
- 80.86.8083
- 84.40.7130
- 86.10.0036
- 84.30.6614
- 8.7.770
- 84.50.7526
- 80.90.5592
- 86.40.0170
- 84.10.5530
- 85.00.0007
- 80.88.4122
- 8.4.254
- 83.30.4036
- 82.50.1602
- 86.50.0190
- 80.82.4063
- 86.26.6008
- 8.4.237
- 8.8.145
- 80.96.6685
- 86.60.0185
- 82.00.9089
- 88.20.0180
- 86.70.0106
- 85.40.2076
- 80.80.2060
- 87.52.2005
- 8.7.115
- 86.50.0263
- 81.20.7481
- 84.20.6108
- 83.00.2095
- 8.7.119
- 80.88.0111
- 82.10.9575
- 80.90.5608
- 86.25.5099
- 83.20.3692
- 88.60.0087
- 8.3.937
- 85.30.1613
- 82.50.1647
- 87.51.1016
If you're planning to uninstall Check Point Endpoint Security you should check if the following data is left behind on your PC.
Folders remaining:
- C:\Program Files (x86)\CheckPoint\Endpoint Security
Check for and remove the following files from your disk when you uninstall Check Point Endpoint Security:
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\BladeEssentialsActors.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\CertUtil.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\cpopenssl.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\DafDaAdaptor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\DataStruct_.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epab.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epab_svc.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabBotChecker.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabCloudReporter.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabCmi.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabCmiUpdater.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabDafAdaptor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabMalwareLib.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabPMLibWrapper.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabRemediation.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabUIAdaptor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabURLInterceptor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabURLInterceptorStub.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabUtils.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabWS.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\ZdxAdaptor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\BackupDriver\cpbak.cat
- C:\Program Files (x86)\CheckPoint\Endpoint Security\BackupDriver\cpbak.inf
- C:\Program Files (x86)\CheckPoint\Endpoint Security\BackupDriver\cpbak.sys
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\Compliance.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\ComplianceAPI.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\expapply.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\fix_log4shell.ps1
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\icslta.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\Ivanti.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\ivanti\7z.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\ivanti\CL5.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\ivanti\SafeReboot.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\ivanti\SafeReboot64.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\ivanti\STDeploy.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\IvantiCB.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\STCore.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\STDeployment.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\STEnginesCatalog.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\STManifestSynchronizer.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\STMetadataExporter.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\STPackager.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\STPatchScanner.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\STServiceProcess.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\7799
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\AntiRansomware.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\ARCleaner.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\AssemblyResolver.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\BackupAndRestoration.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\CP_AmsiProvider32.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\CP_AmsiProvider64.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cpbaklib.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cpdevmon64.sys
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cpdhnypt.inf
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cpdhnypt.sys
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cpdiskflt.inf
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cpdiskflt.sys
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cpefrcli.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cpepmon.cat
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cpepmon.inf
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cpepmon.sys
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cphnet4x.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cphnetldr32.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cphnetldr64.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cphnt32.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cphnt64.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\CPHook.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cphusr32.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\cphusr64.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\damagesConfig.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\DataCollection.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\DCPolicy.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\DCPolicy_ZA.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\devmonapi.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\Dia2Lib.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRGenConf
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRGenSmartExclusionGlobalConf
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_AR.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_DISKVOLUME.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_ENV.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_FLT.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_INJECT.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_IOCTL.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_NET.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_PS.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_REG.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_REGDETECT.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRSAL_SCRIPTS.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\EFRService.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\FltSalConfig.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\HarmonyAddin.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\HarmonyAddin.vsto
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\indicators\Camouflage.out.tmp
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\indicators\Camouflage.xml.tmp
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\indicators\HashCopy.out.tmp
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\indicators\HashCopy.xml.tmp
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\indicators\MLConfig.xml.tmp
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\indicators\mldata.zip
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\indicators\UID1000000.json.tmp
- C:\Program Files (x86)\CheckPoint\Endpoint Security\EFR\indicators\UID1000000_info.json.tmp
Registry keys:
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\93D39ADCED5916649AFFB691AE50AC13
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall\{CDA93D39-95DE-4661-A9FF-6B19EA05CA31}
Additional values that you should remove:
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\93D39ADCED5916649AFFB691AE50AC13\ProductName
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files (x86)\CheckPoint\Endpoint Security\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\WINDOWS\Installer\{CDA93D39-95DE-4661-A9FF-6B19EA05CA31}\
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Check Point Device Auxiliary Framework\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\CPCompliance\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\CPDA\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\CPEFR\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\EpabService\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\EPClientUIService\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\EPWD\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\ISWKL\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\TESvc\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\TracSrvWrapper\ImagePath
How to erase Check Point Endpoint Security from your PC with Advanced Uninstaller PRO
Check Point Endpoint Security is a program marketed by the software company Check Point Software Technologies Ltd.. Some users want to remove it. Sometimes this can be difficult because deleting this by hand takes some experience related to removing Windows applications by hand. The best SIMPLE manner to remove Check Point Endpoint Security is to use Advanced Uninstaller PRO. Here are some detailed instructions about how to do this:1. If you don't have Advanced Uninstaller PRO on your Windows system, install it. This is good because Advanced Uninstaller PRO is a very potent uninstaller and general utility to clean your Windows system.
DOWNLOAD NOW
- go to Download Link
- download the program by clicking on the green DOWNLOAD button
- install Advanced Uninstaller PRO
3. Click on the General Tools button
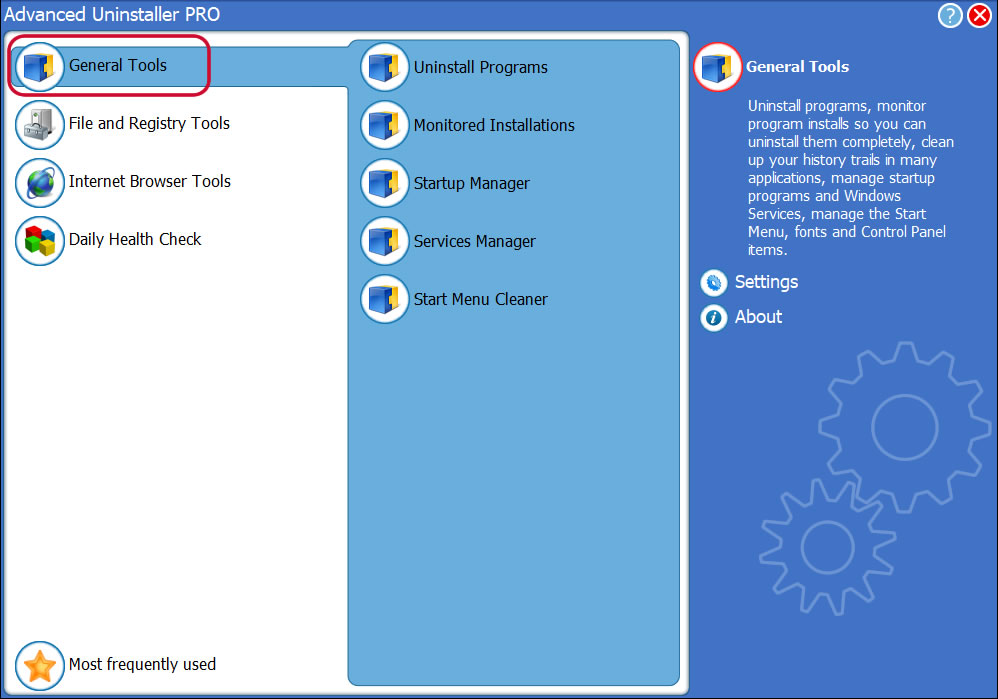
4. Activate the Uninstall Programs feature
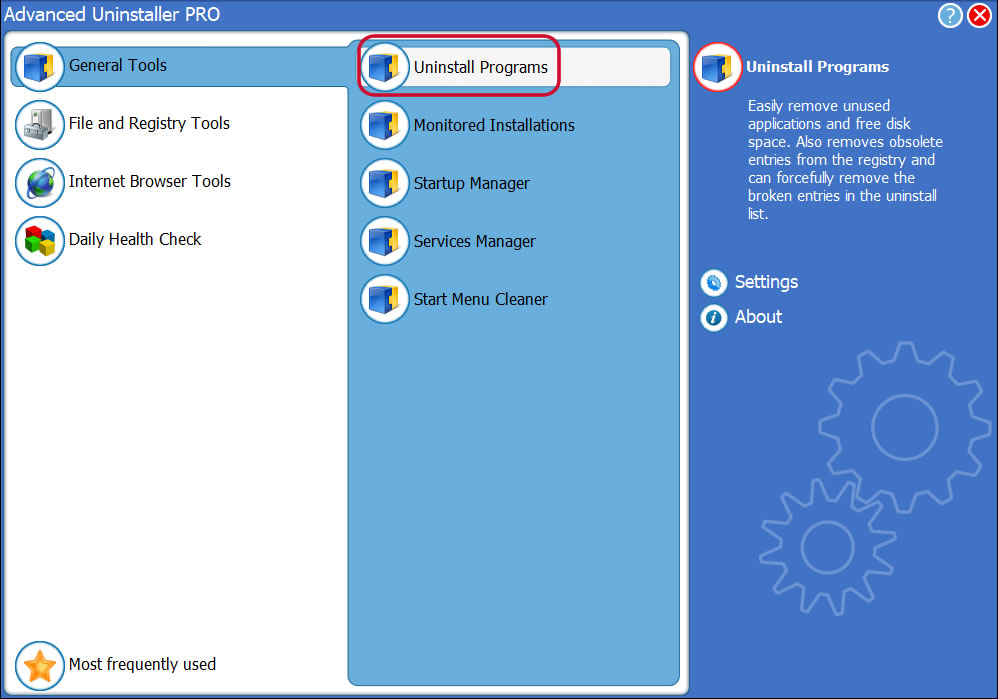
5. All the programs installed on the PC will appear
6. Navigate the list of programs until you locate Check Point Endpoint Security or simply activate the Search field and type in "Check Point Endpoint Security". The Check Point Endpoint Security app will be found automatically. When you click Check Point Endpoint Security in the list of programs, the following information about the program is shown to you:
- Star rating (in the lower left corner). The star rating tells you the opinion other users have about Check Point Endpoint Security, from "Highly recommended" to "Very dangerous".
- Reviews by other users - Click on the Read reviews button.
- Technical information about the app you want to remove, by clicking on the Properties button.
- The publisher is: http://www.checkpoint.com
- The uninstall string is: MsiExec.exe /X{D84FA1D7-7063-4021-B1E3-3C002F53F516}
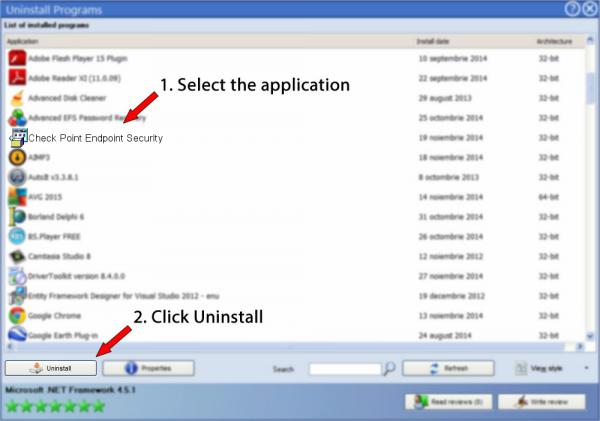
8. After removing Check Point Endpoint Security, Advanced Uninstaller PRO will offer to run an additional cleanup. Click Next to proceed with the cleanup. All the items of Check Point Endpoint Security that have been left behind will be detected and you will be asked if you want to delete them. By removing Check Point Endpoint Security with Advanced Uninstaller PRO, you are assured that no Windows registry items, files or directories are left behind on your system.
Your Windows PC will remain clean, speedy and ready to take on new tasks.
Disclaimer
The text above is not a piece of advice to remove Check Point Endpoint Security by Check Point Software Technologies Ltd. from your PC, we are not saying that Check Point Endpoint Security by Check Point Software Technologies Ltd. is not a good software application. This page simply contains detailed info on how to remove Check Point Endpoint Security in case you want to. Here you can find registry and disk entries that Advanced Uninstaller PRO stumbled upon and classified as "leftovers" on other users' PCs.
2024-01-17 / Written by Daniel Statescu for Advanced Uninstaller PRO
follow @DanielStatescuLast update on: 2024-01-17 06:32:07.730