 Check Point Endpoint Security
Check Point Endpoint Security
A way to uninstall Check Point Endpoint Security from your PC
This page contains thorough information on how to uninstall Check Point Endpoint Security for Windows. It was developed for Windows by Check Point Software Technologies Ltd.. You can read more on Check Point Software Technologies Ltd. or check for application updates here. Please follow http://www.checkpoint.com if you want to read more on Check Point Endpoint Security on Check Point Software Technologies Ltd.'s page. The program is usually placed in the C:\Program Files (x86)\CheckPoint\Endpoint Security directory (same installation drive as Windows). Check Point Endpoint Security's complete uninstall command line is MsiExec.exe /X{811BAF75-5BAC-4698-9638-91B169C5AB25}. The program's main executable file is named chkdat32.exe and it has a size of 113.24 KB (115960 bytes).The executables below are part of Check Point Endpoint Security. They occupy an average of 104.58 MB (109659832 bytes) on disk.
- chkdat32.exe (113.24 KB)
- cpinfo.exe (675.24 KB)
- disknet.exe (31.57 MB)
- fe.exe (887.02 KB)
- InstallDeviceFilterDriver.exe (127.24 KB)
- KAEon.exe (179.74 KB)
- SelectUsersSrv.exe (25.74 KB)
- ServiceRequest.exe (100.74 KB)
- unlock.exe (1.41 MB)
- unlock_ntfs.exe (20.30 MB)
- MeDrInst.exe (60.77 KB)
- cpda.exe (1.73 MB)
- CPRegSvr.exe (135.66 KB)
- cpvinfo.exe (63.36 KB)
- dlg.exe (191.27 KB)
- dnuninst.exe (173.24 KB)
- EP_CDT.exe (44.11 KB)
- fwcpp.exe (33.49 KB)
- IDAFServerHostService.exe (217.27 KB)
- PacketMon.exe (165.50 KB)
- PushOperationsRepairHelper.exe (90.77 KB)
- CRSValidator.exe (103.66 KB)
- cpinfo.exe (163.77 KB)
- CpInfoPreboot.exe (616.27 KB)
- DumpSMBios.exe (67.27 KB)
- ListInstalledApps.exe (72.27 KB)
- ListPartitions.exe (98.27 KB)
- lspol.exe (48.00 KB)
- cpinfo_uploader.exe (5.61 MB)
- DAAW.exe (235.77 KB)
- openmail.exe (33.77 KB)
- trac.exe (1.51 MB)
- TracCAPI.exe (861.27 KB)
- TracSrvWrapper.exe (5.43 MB)
- TrGUI.exe (17.27 MB)
- update_config_tool.exe (322.77 KB)
- vna_install64.exe (18.54 KB)
- vna_utils.exe (71.65 KB)
- VPN_ProxyServer.exe (100.54 KB)
- drvslv7x.exe (1.14 MB)
- fdecontrol.exe (1.14 MB)
- FDE_Drive_Slaving.exe (1.80 MB)
- UseRec.exe (926.77 KB)
- CPEPNotifier.exe (47.24 KB)
- cptrayLogic.exe (13.74 KB)
- cptrayUI.exe (96.24 KB)
- logProcessor.exe (121.74 KB)
- HotspotApplication.exe (14.24 KB)
- wkhtmltopdf.exe (8.17 MB)
- EPWD.exe (286.27 KB)
- EPWD_Tool.exe (62.77 KB)
The current web page applies to Check Point Endpoint Security version 80.80.2060 only. You can find below a few links to other Check Point Endpoint Security releases:
- 81.00.7062
- 86.80.0109
- 8.4.196
- 8.6.533
- 8.2.965
- 80.94.6538
- 80.72.0078
- 84.71.8708
- 80.70.0209
- 8.4.152
- 80.65.2516
- 8.2.897
- 84.30.6638
- 8.8.388
- 8.4.620
- 8.7.036
- 80.70.0363
- 80.72.0054
- 85.00.0017
- 84.00.5003
- 8.2.954
- 86.40.0169
- 84.70.8619
- 80.84.6075
- 8.4.213
- 86.30.0187
- 87.00.0022
- 80.95.6601
- 86.40.0242
- 80.94.6519
- 80.87.9201
- 87.31.1015
- 80.70.0247
- 85.20.1115
- 82.40.1102
- 80.83.5080
- 88.10.0220
- 86.01.1005
- 87.31.1016
- 86.25.5060
- 86.00.0007
- 80.85.7064
- 8.4.467
- 8.2.833
- 83.15.3054
- 87.62.2002
- 82.30.0530
- 80.87.9250
- 87.30.0232
- 8.7.025
- 8.3.755
- 80.87.9084
- 86.51.1013
- 88.00.0188
- 8.2.898
- 8.8.255
- 84.60.8134
- 8.2.923
- 80.86.8083
- 84.40.7130
- 86.10.0036
- 84.30.6614
- 8.7.770
- 84.50.7526
- 80.90.5592
- 86.40.0170
- 84.10.5530
- 85.00.0007
- 80.88.4122
- 8.4.254
- 83.30.4036
- 82.50.1602
- 86.50.0190
- 80.82.4063
- 86.26.6008
- 8.4.237
- 8.8.145
- 80.96.6685
- 86.60.0185
- 82.00.9089
- 88.20.0180
- 86.70.0106
- 85.40.2076
- 87.52.2005
- 8.7.115
- 86.50.0263
- 81.20.7481
- 84.20.6108
- 83.00.2095
- 8.7.119
- 80.88.0111
- 82.10.9575
- 80.90.5608
- 86.25.5099
- 83.20.3692
- 88.60.0087
- 8.3.937
- 85.30.1613
- 82.50.1647
- 87.51.1016
If you're planning to uninstall Check Point Endpoint Security you should check if the following data is left behind on your PC.
You should delete the folders below after you uninstall Check Point Endpoint Security:
- C:\Program Files (x86)\CheckPoint\Endpoint Security
The files below remain on your disk when you remove Check Point Endpoint Security:
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\3DCompliance.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\3DReportPolicy.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\BladeFoundation.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\Compliance.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\Epilogue.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Compliance\icslta.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\apputils.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\BladeFoundation.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\caCert.txt
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\ccore32.bin
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\CloudServices.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\CommonClientSettings.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\COMSecurityPS.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\comutils.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\config.bak
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\CP.UEPM.Console.FDE.Authentication.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cp_policy.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\CP_version_info.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cpbcrypt.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cpcert.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cpcryptutil.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cpda.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cpexpat.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\CPHook.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cplogluuid.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cplogrepository.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cpopenssl.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cpprng.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cppsm.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\CPRegSvr.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cpsrvis.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cpvinfo.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cpxerces_c.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cryptocore.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\cvars.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\DAF_dsm.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\daf_logger.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\DafStub.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\DataStruct.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\DeviceAgentAPI.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\dlg.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\dnuninst.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\Encode.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\EP_CDT.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\Epilogue.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\EventUtils.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\fdt.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\findmsi.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\fwcpp.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\fwmonitor.def
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\iDAFServer.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\IDAFServerHostService.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\IItoolBox.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\ISWKL.sys
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\ISWWH.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\KerberosClient.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\KerberosCommon.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\libcurl.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\lmx-MD-vc9.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\messaging.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\OS.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\PacketMon.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\preupg.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\ProdUtils.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\ProviderStore.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\PushOperationsClient.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\PushOperationsRepairHelper.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\regError.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\Resolve.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\sic.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\tcpip.def
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\UepmLogSchemaLib.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\UepmLogXformLib.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\wow64\CPHook.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\wow64\ISWWH.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\ZDx.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\crs.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\CRSValidator.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.11.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.12.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.13.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.15.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.16.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.17.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.19.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.20.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.21.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.22.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.23.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.24.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.25.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.26.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.27.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.28.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.30.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.40.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.41.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.42.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\Conf\LogConvertorSchema.43.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\cpinfo\ClientUI.ini
You will find in the Windows Registry that the following keys will not be removed; remove them one by one using regedit.exe:
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\57FAB118CAB589646983191B965CBA52
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall\{811BAF75-5BAC-4698-9638-91B169C5AB25}
Use regedit.exe to delete the following additional values from the Windows Registry:
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\57FAB118CAB589646983191B965CBA52\ProductName
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files (x86)\CheckPoint\Endpoint Security\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\WINDOWS\Installer\{811BAF75-5BAC-4698-9638-91B169C5AB25}\
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Check Point Device Auxiliary Framework\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\CPCompliance\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\CPDA\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\EPClientUIService\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\EPWD\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\ISWKL\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\TracSrvWrapper\ImagePath
How to uninstall Check Point Endpoint Security from your computer with the help of Advanced Uninstaller PRO
Check Point Endpoint Security is a program by the software company Check Point Software Technologies Ltd.. Sometimes, computer users want to uninstall this application. Sometimes this can be troublesome because deleting this manually takes some advanced knowledge related to PCs. One of the best EASY procedure to uninstall Check Point Endpoint Security is to use Advanced Uninstaller PRO. Here is how to do this:1. If you don't have Advanced Uninstaller PRO on your Windows PC, add it. This is a good step because Advanced Uninstaller PRO is a very potent uninstaller and general tool to clean your Windows PC.
DOWNLOAD NOW
- visit Download Link
- download the setup by pressing the green DOWNLOAD NOW button
- set up Advanced Uninstaller PRO
3. Click on the General Tools category
4. Press the Uninstall Programs button
5. All the programs existing on the PC will be shown to you
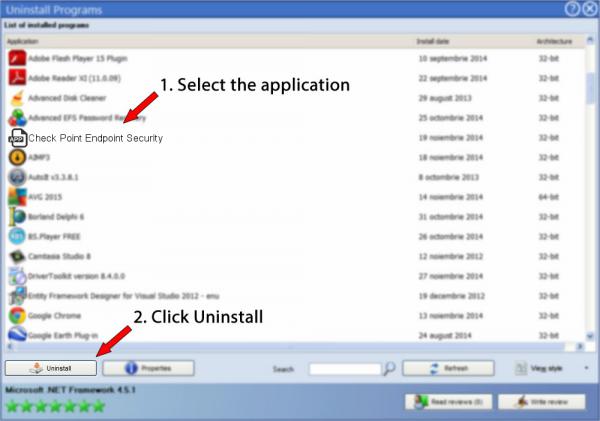
6. Scroll the list of programs until you find Check Point Endpoint Security or simply activate the Search feature and type in "Check Point Endpoint Security". The Check Point Endpoint Security program will be found automatically. When you click Check Point Endpoint Security in the list , the following data regarding the application is available to you:
- Star rating (in the lower left corner). This tells you the opinion other people have regarding Check Point Endpoint Security, ranging from "Highly recommended" to "Very dangerous".
- Opinions by other people - Click on the Read reviews button.
- Technical information regarding the application you wish to remove, by pressing the Properties button.
- The publisher is: http://www.checkpoint.com
- The uninstall string is: MsiExec.exe /X{811BAF75-5BAC-4698-9638-91B169C5AB25}
8. After removing Check Point Endpoint Security, Advanced Uninstaller PRO will offer to run a cleanup. Click Next to perform the cleanup. All the items that belong Check Point Endpoint Security that have been left behind will be detected and you will be able to delete them. By uninstalling Check Point Endpoint Security with Advanced Uninstaller PRO, you are assured that no Windows registry items, files or directories are left behind on your system.
Your Windows computer will remain clean, speedy and able to run without errors or problems.
Disclaimer
This page is not a piece of advice to uninstall Check Point Endpoint Security by Check Point Software Technologies Ltd. from your PC, we are not saying that Check Point Endpoint Security by Check Point Software Technologies Ltd. is not a good application. This page only contains detailed info on how to uninstall Check Point Endpoint Security supposing you decide this is what you want to do. The information above contains registry and disk entries that Advanced Uninstaller PRO stumbled upon and classified as "leftovers" on other users' computers.
2018-04-01 / Written by Andreea Kartman for Advanced Uninstaller PRO
follow @DeeaKartmanLast update on: 2018-04-01 15:09:55.740