 Check Point Endpoint Security
Check Point Endpoint Security
A guide to uninstall Check Point Endpoint Security from your PC
Check Point Endpoint Security is a software application. This page contains details on how to uninstall it from your computer. It is written by Check Point Software Technologies Ltd.. Check out here for more info on Check Point Software Technologies Ltd.. Please follow http://www.checkpoint.com if you want to read more on Check Point Endpoint Security on Check Point Software Technologies Ltd.'s website. Check Point Endpoint Security is typically installed in the C:\Program Files (x86)\CheckPoint\Endpoint Security Agent directory, but this location can vary a lot depending on the user's decision when installing the application. The full command line for removing Check Point Endpoint Security is MsiExec.exe /X{BF386B05-6DFF-4439-AE28-A994E281B8B3}. Keep in mind that if you will type this command in Start / Run Note you may get a notification for administrator rights. The application's main executable file occupies 3.78 MB (3967168 bytes) on disk and is named cpda.exe.Check Point Endpoint Security is composed of the following executables which take 16.18 MB (16962208 bytes) on disk:
- cpda.exe (3.78 MB)
- CPRegSvr.exe (90.24 KB)
- cptray_mini.exe (294.19 KB)
- cpvinfo.exe (71.74 KB)
- dlg.exe (212.19 KB)
- IDAFServerHostService.exe (648.19 KB)
- PushOperationsRepairHelper.exe (366.19 KB)
- cpinfo.exe (518.19 KB)
- cpinfoUI.exe (219.69 KB)
- lspol.exe (48.00 KB)
- cpinfo_uploader.exe (6.27 MB)
- tracelog.exe (83.69 KB)
- tracelog.exe (91.19 KB)
- nginx.exe (3.54 MB)
This info is about Check Point Endpoint Security version 84.70.8619 alone. Click on the links below for other Check Point Endpoint Security versions:
- 81.00.7062
- 86.80.0109
- 8.4.196
- 8.6.533
- 8.2.965
- 80.94.6538
- 80.72.0078
- 84.71.8708
- 80.70.0209
- 8.4.152
- 80.65.2516
- 8.2.897
- 84.30.6638
- 8.8.388
- 8.4.620
- 8.7.036
- 80.70.0363
- 80.72.0054
- 85.00.0017
- 84.00.5003
- 8.2.954
- 86.40.0169
- 80.84.6075
- 8.4.213
- 86.30.0187
- 87.00.0022
- 80.95.6601
- 86.40.0242
- 80.94.6519
- 80.87.9201
- 87.31.1015
- 80.70.0247
- 85.20.1115
- 82.40.1102
- 80.83.5080
- 88.10.0220
- 86.01.1005
- 87.31.1016
- 86.25.5060
- 86.00.0007
- 80.85.7064
- 8.4.467
- 8.2.833
- 83.15.3054
- 87.62.2002
- 82.30.0530
- 80.87.9250
- 87.30.0232
- 8.7.025
- 8.3.755
- 80.87.9084
- 86.51.1013
- 88.00.0188
- 8.2.898
- 8.8.255
- 84.60.8134
- 8.2.923
- 80.86.8083
- 84.40.7130
- 86.10.0036
- 84.30.6614
- 8.7.770
- 84.50.7526
- 80.90.5592
- 86.40.0170
- 84.10.5530
- 85.00.0007
- 80.88.4122
- 8.4.254
- 83.30.4036
- 82.50.1602
- 86.50.0190
- 80.82.4063
- 86.26.6008
- 8.4.237
- 8.8.145
- 80.96.6685
- 86.60.0185
- 82.00.9089
- 88.20.0180
- 86.70.0106
- 85.40.2076
- 80.80.2060
- 87.52.2005
- 8.7.115
- 86.50.0263
- 81.20.7481
- 84.20.6108
- 83.00.2095
- 8.7.119
- 80.88.0111
- 82.10.9575
- 80.90.5608
- 86.25.5099
- 83.20.3692
- 88.60.0087
- 8.3.937
- 85.30.1613
- 82.50.1647
- 87.51.1016
Some files and registry entries are typically left behind when you remove Check Point Endpoint Security.
Folders left behind when you uninstall Check Point Endpoint Security:
- C:\Program Files (x86)\CheckPoint\Endpoint Security
Check for and delete the following files from your disk when you uninstall Check Point Endpoint Security:
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\BladeEssentialsActors.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\DafDaAdaptor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\DataStruct_.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epab.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epab_svc.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabBotChecker.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabCloudReporter.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabCmi.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabCmiUpdater.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabDafAdaptor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabMalwareLib.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabPMLibWrapper.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabRemediation.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabUIAdaptor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabURLInterceptor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabURLInterceptorStub.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabUtils.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\epabWS.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\AntiBot\ZdxAdaptor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\AntiMalwareAPI.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\ac_facade.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\ac_meta.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\acassembler.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\agreements.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\am_core.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\am_facade_embedded.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\am_facade_server.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\am_meta.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\am_patch_management.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\am_remote_client.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\am_remote_server.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\am_win_aux.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\app_control.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\app_control_prague.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\app_core.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\app_core_etw.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\app_core_legacy.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\app_core_meta.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\application_categorizer.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\application_investigator.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\audio_processor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\avstream_monitor.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\base64.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\bi_facade.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\bi_meta.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\btdisk.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\btimages.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\buffer.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\cf_engines.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\cf_engines_meta.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\cf_facade.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\CKAHComm.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\ckahrule.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\CKAHUM.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Cleanup.reg
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Cleanup64.reg
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\clldr.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\config.esm
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\configuration.esm
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\content_filtering_meta.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\crpthlpr.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\crypto_components.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\crypto_components_meta.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\crypto_services.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\crypto_ssl.config
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\DataFormats-en.xml
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\dblite.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\dmap.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\dns_client.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\dtreg.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\ekasyswatch.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\EntAppControlTask.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\enterprise_application_control.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\ExtScanMon.exe
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\FileCategorizer.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\filesystem_services.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\format_recognizer.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\FsDrvPlg.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\fssync.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\fssync_s.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\hashmd5.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\hashsha1.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\hips.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\hips_perf_meta.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\icudt58.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\icuin58.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\icuio58.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\icuuc58.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\inifile.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\DIFxAPI.dll
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\instdrivers\kl1\x64\kl1.cat
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\instdrivers\kl1\x64\kl1.inf
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\instdrivers\kl1\x64\kl1.sys
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\instdrivers\kl1\x64\klbg_uninstall.reg
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\instdrivers\kl1\x64\klwtp.cat
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\instdrivers\kl1\x64\klwtp.inf
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\instdrivers\kl1\x64\klwtp.sys
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\instdrivers\kl1\x64\Win8\klelam.cat
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\instdrivers\kl1\x64\Win8\klelam.inf
- C:\Program Files (x86)\CheckPoint\Endpoint Security\Anti-Malware\Avsys\Install\instdrivers\kl1\x64\Win8\klelam.sys
Registry keys:
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\FCD105D6B453B53488147D1F96F92E81
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall\{6D501DCF-354B-435B-8841-D7F1699FE218}
Open regedit.exe in order to remove the following values:
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\FCD105D6B453B53488147D1F96F92E81\ProductName
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files (x86)\CheckPoint\Endpoint Security\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\WINDOWS\Installer\{6D501DCF-354B-435B-8841-D7F1699FE218}\
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Check Point Device Auxiliary Framework\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\CPCompliance\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\CPDA\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\CPEFR\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\EpabService\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\EpamService\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\EPClientUIService\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\EPWD\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\gwcc\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\ISWKL\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\RemediationService\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\TESvc\ImagePath
- HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\TracSrvWrapper\ImagePath
How to erase Check Point Endpoint Security from your computer with Advanced Uninstaller PRO
Check Point Endpoint Security is an application offered by Check Point Software Technologies Ltd.. Frequently, people choose to erase it. This is difficult because uninstalling this manually requires some advanced knowledge related to removing Windows programs manually. The best SIMPLE solution to erase Check Point Endpoint Security is to use Advanced Uninstaller PRO. Take the following steps on how to do this:1. If you don't have Advanced Uninstaller PRO already installed on your PC, install it. This is a good step because Advanced Uninstaller PRO is an efficient uninstaller and general utility to take care of your system.
DOWNLOAD NOW
- go to Download Link
- download the program by clicking on the green DOWNLOAD NOW button
- install Advanced Uninstaller PRO
3. Click on the General Tools category
4. Press the Uninstall Programs tool
5. All the programs installed on your PC will appear
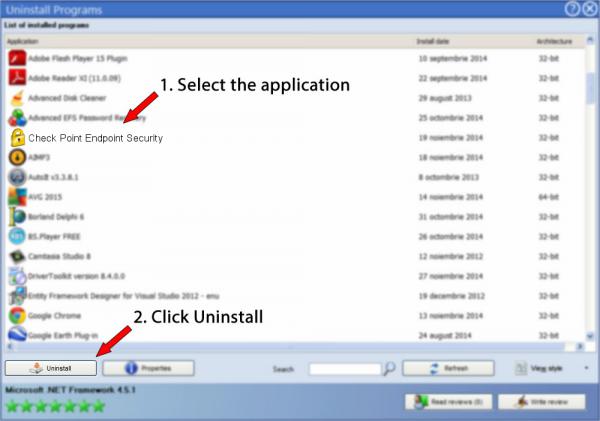
6. Scroll the list of programs until you find Check Point Endpoint Security or simply activate the Search feature and type in "Check Point Endpoint Security". If it is installed on your PC the Check Point Endpoint Security app will be found automatically. Notice that after you select Check Point Endpoint Security in the list , some data about the application is made available to you:
- Star rating (in the left lower corner). This explains the opinion other people have about Check Point Endpoint Security, from "Highly recommended" to "Very dangerous".
- Reviews by other people - Click on the Read reviews button.
- Technical information about the application you wish to remove, by clicking on the Properties button.
- The publisher is: http://www.checkpoint.com
- The uninstall string is: MsiExec.exe /X{BF386B05-6DFF-4439-AE28-A994E281B8B3}
8. After uninstalling Check Point Endpoint Security, Advanced Uninstaller PRO will offer to run an additional cleanup. Press Next to perform the cleanup. All the items of Check Point Endpoint Security which have been left behind will be detected and you will be asked if you want to delete them. By removing Check Point Endpoint Security using Advanced Uninstaller PRO, you are assured that no Windows registry items, files or directories are left behind on your PC.
Your Windows system will remain clean, speedy and ready to take on new tasks.
Disclaimer
The text above is not a recommendation to remove Check Point Endpoint Security by Check Point Software Technologies Ltd. from your computer, nor are we saying that Check Point Endpoint Security by Check Point Software Technologies Ltd. is not a good application for your PC. This page simply contains detailed instructions on how to remove Check Point Endpoint Security in case you want to. Here you can find registry and disk entries that our application Advanced Uninstaller PRO discovered and classified as "leftovers" on other users' PCs.
2022-07-06 / Written by Dan Armano for Advanced Uninstaller PRO
follow @danarmLast update on: 2022-07-06 14:26:37.220