 McAfee Endpoint Security 威胁防护
McAfee Endpoint Security 威胁防护
How to uninstall McAfee Endpoint Security 威胁防护 from your system
McAfee Endpoint Security 威胁防护 is a software application. This page contains details on how to uninstall it from your computer. It is made by McAfee, LLC.. Check out here where you can find out more on McAfee, LLC.. Click on http://www.mcafeesecurity.com/ to get more facts about McAfee Endpoint Security 威胁防护 on McAfee, LLC.'s website. Usually the McAfee Endpoint Security 威胁防护 application is installed in the C:\Program Files\McAfee\Endpoint Security folder, depending on the user's option during install. You can remove McAfee Endpoint Security 威胁防护 by clicking on the Start menu of Windows and pasting the command line MsiExec.exe /X{21A798B9-A5A1-49D7-9F96-CC8B14F7EAEF}. Note that you might get a notification for admin rights. McAfee Endpoint Security 威胁防护's main file takes around 150.39 KB (154000 bytes) and its name is ESConfigTool.exe.McAfee Endpoint Security 威胁防护 installs the following the executables on your PC, occupying about 9.83 MB (10307336 bytes) on disk.
- ESConfigTool.exe (150.39 KB)
- mfeesp.exe (249.86 KB)
- mfeProvisionModeUtility.exe (171.24 KB)
- PwdUninstall.exe (2.67 MB)
- CCUninst.exe (46.43 KB)
- setupCC.exe (860.65 KB)
- MfeUpgradeTool.exe (155.95 KB)
- amcfg.exe (287.45 KB)
- mfeensppl.exe (833.64 KB)
- mfetp.exe (241.80 KB)
- mcshield.exe (1.36 MB)
- mfeamcin.exe (2.15 MB)
- setupTP.exe (745.01 KB)
This web page is about McAfee Endpoint Security 威胁防护 version 10.6.11910 only. Click on the links below for other McAfee Endpoint Security 威胁防护 versions:
...click to view all...
If you are manually uninstalling McAfee Endpoint Security 威胁防护 we recommend you to verify if the following data is left behind on your PC.
Directories found on disk:
- C:\Program Files\McAfee\Endpoint Security
The files below were left behind on your disk by McAfee Endpoint Security 威胁防护 when you uninstall it:
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\AacEventManager.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\AmcEventManager.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\AMCoreUtil.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-console-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-datetime-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-debug-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-errorhandling-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-file-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-file-l1-2-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-file-l2-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-handle-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-heap-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-interlocked-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-libraryloader-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-localization-l1-2-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-memory-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-namedpipe-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-processenvironment-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-processthreads-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-processthreads-l1-1-1.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-profile-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-rtlsupport-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-string-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-synch-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-synch-l1-2-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-sysinfo-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-timezone-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-core-util-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-conio-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-convert-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-environment-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-filesystem-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-heap-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-locale-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-math-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-multibyte-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-private-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-process-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-runtime-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-stdio-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-string-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-time-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\api-ms-win-crt-utility-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\ATP.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\ATP.xml
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\ATP.xsd
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\atp_hss_lpc.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\atp_ma.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\ATP_SelfProtection.rul
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\atpconfigtool.exe
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\ATPDefXlateMap.xml
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\ATPErrMgr.exe
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\blframework.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\concrt140.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\DataUtils.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0404\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0407\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0409\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\040C\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\040D\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0410\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0411\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0412\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0413\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0415\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0416\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0419\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\041D\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0804\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\lang\0C0A\strings.bin
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\Loglib.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\McVariantExport.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\mfeatp.exe
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\mfeatp_profile.xml
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\msvcp140.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\RemediationBO.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\RepairCache\2052.mst
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\RepairCache\McAfee_Adaptive_Threat_Protection_x64.msi
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\RepairCache\setupATP.exe
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\ScanOrchestrator.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\sm.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\ucrtbase.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\vccorlib140.dll
- C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\vcruntime140.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\ap.bak.xml
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\ap.xml
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\ap.xsd
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\ApBl.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\ApBlEventMap.xml
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-console-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-datetime-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-debug-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-errorhandling-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-file-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-file-l1-2-0.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-file-l2-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-handle-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-heap-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-interlocked-l1-1-0.dll
- C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\api-ms-win-core-libraryloader-l1-1-0.dll
Generally the following registry data will not be removed:
- HKEY_CURRENT_USER\Software\McAfee Endpoint Security
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\4DEA37B5EBABD0F4FB34CBADB4FBB6F7
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\9B897A121A5A7D94F969CCB8417FAEFE
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\A8D65C5AD1289944094BD5C66FAB6A8D
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\C54D3A36D0FECA04BA94E3CD3CC6E586
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\D81ED61BD5D48F5429DBD81C2752FA8D
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall\{21A798B9-A5A1-49D7-9F96-CC8B14F7EAEF}
- HKEY_LOCAL_MACHINE\Software\Wow6432Node\McAfee_Endpoint_Security_CustomAction_Logging_10.6
- HKEY_LOCAL_MACHINE\Software\Wow6432Node\McAfee_Endpoint_Security_CustomAction_Logging_10.7
Additional registry values that you should remove:
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\4DEA37B5EBABD0F4FB34CBADB4FBB6F7\ProductName
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\9B897A121A5A7D94F969CCB8417FAEFE\ProductName
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\A8D65C5AD1289944094BD5C66FAB6A8D\ProductName
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\C54D3A36D0FECA04BA94E3CD3CC6E586\ProductName
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\D81ED61BD5D48F5429DBD81C2752FA8D\ProductName
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\lang\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\Microsoft.UniversalCRT\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\Microsoft.VC140.CRT\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\Microsoft.VC80.CRT\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\RepairCache\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files\McAfee\Endpoint Security\Firewall\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Program Files\McAfee\Endpoint Security\Threat Prevention\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Installer\Folders\C:\Windows\Installer\{21A798B9-A5A1-49D7-9F96-CC8B14F7EAEF}\
A way to erase McAfee Endpoint Security 威胁防护 using Advanced Uninstaller PRO
McAfee Endpoint Security 威胁防护 is a program released by the software company McAfee, LLC.. Some users decide to uninstall this application. This can be troublesome because uninstalling this manually takes some skill related to removing Windows applications by hand. The best QUICK practice to uninstall McAfee Endpoint Security 威胁防护 is to use Advanced Uninstaller PRO. Here is how to do this:1. If you don't have Advanced Uninstaller PRO already installed on your system, install it. This is a good step because Advanced Uninstaller PRO is a very potent uninstaller and all around tool to optimize your computer.
DOWNLOAD NOW
- go to Download Link
- download the program by pressing the DOWNLOAD NOW button
- set up Advanced Uninstaller PRO
3. Click on the General Tools category
4. Press the Uninstall Programs button
5. All the programs installed on your PC will be made available to you
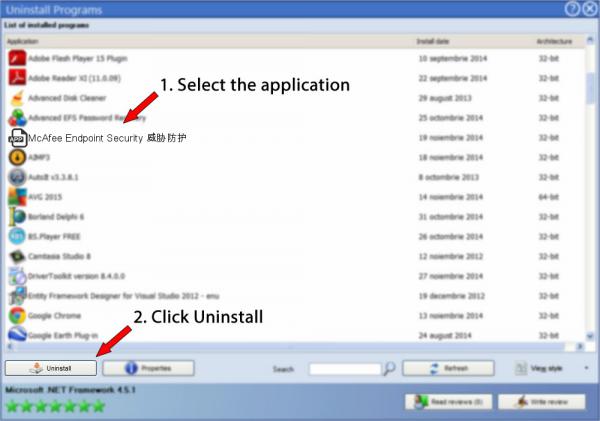
6. Scroll the list of programs until you find McAfee Endpoint Security 威胁防护 or simply click the Search field and type in "McAfee Endpoint Security 威胁防护". If it exists on your system the McAfee Endpoint Security 威胁防护 app will be found very quickly. Notice that when you click McAfee Endpoint Security 威胁防护 in the list of apps, some information about the application is available to you:
- Star rating (in the left lower corner). This tells you the opinion other people have about McAfee Endpoint Security 威胁防护, ranging from "Highly recommended" to "Very dangerous".
- Opinions by other people - Click on the Read reviews button.
- Details about the program you are about to remove, by pressing the Properties button.
- The web site of the program is: http://www.mcafeesecurity.com/
- The uninstall string is: MsiExec.exe /X{21A798B9-A5A1-49D7-9F96-CC8B14F7EAEF}
8. After uninstalling McAfee Endpoint Security 威胁防护, Advanced Uninstaller PRO will ask you to run a cleanup. Click Next to perform the cleanup. All the items of McAfee Endpoint Security 威胁防护 which have been left behind will be found and you will be able to delete them. By removing McAfee Endpoint Security 威胁防护 with Advanced Uninstaller PRO, you can be sure that no Windows registry items, files or directories are left behind on your PC.
Your Windows computer will remain clean, speedy and able to take on new tasks.
Disclaimer
This page is not a recommendation to uninstall McAfee Endpoint Security 威胁防护 by McAfee, LLC. from your computer, we are not saying that McAfee Endpoint Security 威胁防护 by McAfee, LLC. is not a good software application. This text simply contains detailed info on how to uninstall McAfee Endpoint Security 威胁防护 supposing you decide this is what you want to do. Here you can find registry and disk entries that Advanced Uninstaller PRO stumbled upon and classified as "leftovers" on other users' computers.
2020-02-14 / Written by Dan Armano for Advanced Uninstaller PRO
follow @danarmLast update on: 2020-02-14 18:58:16.783